Before I proceed, for the pedants out there, yes, I know that the Greek Trojan Horse can be viewed as a supply chain attack involving a C-section on a wooden horse, but we’re talking cybersecurity here. OK?
Supply chain attacks have been around for decades. However, reports of such attack wax and wane in the press. Resilience360 reported seeing 290 cybersecurity incidents impacting supply chain entities in 2019. The SolarWinds attack has brought the topic of supply chain cyber-attacks to the forefront. In a 2018 Wall Street Journal investigative report concerning the major attack on the power grid by the Russians, they detailed a distributed supply chain attack involving multiple supply chain vendors. The SolarWinds attack was so successful in part due to the large number of high value targets that use SolarWinds products. The attack against the power grid utilized several supply chain vendors to pull off the attack. Although much of what’s driving an industry predicted to reach over 76 billion USD by 2027 has to do with mobile transactions, I’m going to use the authentication use case for this blog.
 The main problem with passwords is that they authenticate credentials, rather than a person. Locks with keys are fairly resilient to phishing attacks, but they authenticate keys. If you have ever unlocked the door to somebody else’s hotel room with your room key you’ll understand the problem with that. Well, at least the woman in the hotel room that my key wasn’t supposed to unlock understood it. So did the front desk. The code you use for the keyless entry device is a password, and it is the password, and not the individual that is granted access. Once the PIN (password) is in the possession of than authorized individual, compromise is one chocolate bar away. Biometrics identify individuals and as such offer increased physical and digital security. But biometric systems are not free of security concerns, and the first in the ecosystem is the supply chain.
The main problem with passwords is that they authenticate credentials, rather than a person. Locks with keys are fairly resilient to phishing attacks, but they authenticate keys. If you have ever unlocked the door to somebody else’s hotel room with your room key you’ll understand the problem with that. Well, at least the woman in the hotel room that my key wasn’t supposed to unlock understood it. So did the front desk. The code you use for the keyless entry device is a password, and it is the password, and not the individual that is granted access. Once the PIN (password) is in the possession of than authorized individual, compromise is one chocolate bar away. Biometrics identify individuals and as such offer increased physical and digital security. But biometric systems are not free of security concerns, and the first in the ecosystem is the supply chain.
Biometric systems create a unique template for each individual and “enrolls” them in the system. I give my fingerprint and a biometric template which is unique to me is created and stored. When I need to be authenticated the biometric capture device creates a new template and compares it to the stored template. But biometric templates are not perfect. The false acceptance rate (FAR) determines how susceptible the system is to authenticating the wrong person due to mis-identification. I call that the doppelganger effect. The false rejection rate (FRR) measures how often valid biometric measurements are rejected. A high FAR makes it easier to gain unauthorized access. A high FRR can seriously disrupt business as essential access to resources is denied. No system has both a zero FRR and FAR, and the acceptable balance of the two is a matter of risk tolerance.
The biometric kill chain starts upon delivery of the biometric device. Between the time that the device is received and installation is completed lives the first step in this kill chain. A potential attack at this stage would be for the installer to enroll unauthorized biometric data. A device could come with previously enrolled templates. This means that from the start, some form of auditing must be performed.
Next in the biometric kill chain is the input. A biometric input, such as a fingerprint, can be spoofed and then accepted by the capture device. These attacks are real and have sometimes required little sophistication to pull off. Multifactor authentication (MFA) can greatly reduce the success rate for these attacks, but do not combine fingerprint and retina scanning biometrics; that’s how eyes get poked out!
 There are some devices that are essentially stand-alone. These devices can be more secure, however there still must be a way to back up data and perform firmware upgrades, etc. Removable media is one data transfer method, but without a robust handshake protocol between the removable media and the system we have an unauthenticated device (removable media) that is supposed to provide authentic information.
There are some devices that are essentially stand-alone. These devices can be more secure, however there still must be a way to back up data and perform firmware upgrades, etc. Removable media is one data transfer method, but without a robust handshake protocol between the removable media and the system we have an unauthenticated device (removable media) that is supposed to provide authentic information.
 Networked biometric systems add their own attack surfaces and hence add links to the kill chain. Once the biometric data has been captured it will be uploaded to a computer for comparison of the sample to the database containing the enrolled templates. Template insertion attacks are possible between the acquisition device and the database of stored templates. The attack may be performed by injecting a valid template after an attacker uses the device, or more simply the attack can be used to add the attacker’s biometric template to the database. Unsecured S3 buckets or other cloud computing platforms might not be the best place to store biometric data.
Networked biometric systems add their own attack surfaces and hence add links to the kill chain. Once the biometric data has been captured it will be uploaded to a computer for comparison of the sample to the database containing the enrolled templates. Template insertion attacks are possible between the acquisition device and the database of stored templates. The attack may be performed by injecting a valid template after an attacker uses the device, or more simply the attack can be used to add the attacker’s biometric template to the database. Unsecured S3 buckets or other cloud computing platforms might not be the best place to store biometric data.
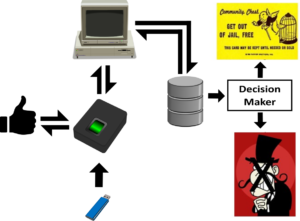 Next comes the decision maker. Once the comparison in the database is done, the pass or fail indicator is sent to the decision maker. Manipulation of the input or the output to the decision maker can change a fail to a pass, or if you’re a big fan of spy thrillers, a pass is changed to a fail in order to keep the security guard out while rolls of toilet paper are being stolen from the bathrooms and supply closets.
Next comes the decision maker. Once the comparison in the database is done, the pass or fail indicator is sent to the decision maker. Manipulation of the input or the output to the decision maker can change a fail to a pass, or if you’re a big fan of spy thrillers, a pass is changed to a fail in order to keep the security guard out while rolls of toilet paper are being stolen from the bathrooms and supply closets.
While there may be several different biometric device topologies, the fundamental functionality is the same. Acquire input, create and store the template, or compare the capture to the existing template, and then decide what happens next. Differences in implementations can change exploitable attack surfaces and so each product must be examined to determine what that specific system’s kill chain looks like.
Biometric authentication can be a far more secure authentication method than passwords, but that does not mean that successful attacks cannot be performed against them. The difference in potential harm from password compromise and biometric template compromise has important legal ramifications that must be considered. You can learn more about the legal implications in my blog “Biometric Legal Implications.”
In the meantime, if you are worried about being denied access because you lost a finger, I suggest you make a backup finger. It should work four out of five times.
Randy Abrams
Senior Security Analyst
SecureIQLab



