Every year, an exorbitant amount of money is spent on ensuring companies’ digital safety, yet data breaches continue to rise. Three main reasons cause this unfortunate event: First, companies often misconfigured the cloud, making the system an easy target. Second, aggressive types of ransomware attacks are on the rise. Third, companies are being too permissive when allowing suppliers access to systems.
According to Harvard Business, 60% of the world’s company data is in the cloud due to its cost-efficient and convenient nature. An abundance of data makes the cloud a desirable target. The Wall Street Journal stated that 82% of data breaches were from the cloud. The cloud isn’t just an attractive target but has commonly misconfigured security products. This can be caused by allowing “excessively permissive” access, unencrypted backups, and unrestricted ports. Due to the cloud’s youth, many companies need to gain knowledge and experience of how to protect their information.
All these factors, combined with the cloud’s developing complexity, can accidentally leave corporate data vulnerable. Overall, most breaches are preventable if companies:
● Ensure trained and empowered individuals can appropriately validate security systems.
● Install processes to ensure repeatability.
● Use appropriate security systems to protect assets.
To avoid configuration errors and check if changes have been made, follow these steps:
- Validate that the cloud configuration is correct.
- Export the configuration file for reference.
- Hash the configuration file.
- Audit the configuration regularly by exporting configuration files and comparing the hash to the original hash to see if there are any changes.
- Automate the process.
- Alert if changes are detected.
Next, ransomware attacks occur when a hacker accesses and encrypts files until a ransom is paid. Recently, these attacks have been less effective due to increased backups, but this doesn’t account for stolen data being released. The FBI recommends using data loss prevention products, which make the data useless to unauthorized individuals and immune to abuse.
Cloudflare also emphasizes that ransomware can often begin as “phishing,” a social engineering attack aimed at acquiring usernames, passwords, and other private information. Imperva agrees that the information acquired could be used to facilitate identity theft and/or be used in other “social engineering attacks.”
Recently, a more aggressive type of ransomware attack has sprouted. IBM states that hackers began to make copies of files to “steal data” and/or threaten to release sensitive information, which is both blackmail and theft. This private data could also be sold as a hot item on the black market. To prevent this process, called exfiltration, it’s essential to:
● Monitor external outputs.
● Close unnecessary ports.
● Encrypt data.
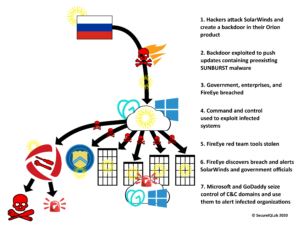
Another major reason for increased data breaches is the exploitation of software vulnerabilities that frequently compromise systems. Lastly, Cloudflare states that “supply chain attacks” are a major cause of data breaches. These can occur when external vendors, such as air conditioning maintenance or software suppliers, have been compromised. These companies are frequently smaller and lack strong cybersecurity, so hackers will “proxy” their systems to target the main company. Once hackers have gained access, they can use the foothold to move laterally and gain increased access to the company’s systems.
Every company must be aware of this type of attack and understand the risk attached to contracting vendors to help reduce exposure. Third-party access should be as limited as possible. Companies’ security can be assessed using apps such as “Bitsight” or “SecurityScorecard.” Once a company is considered safe, it’s important to limit its access and install data loss prevention products (DLP).
Overall, companies must keep up with attack trends, the types of cybersecurity attacks, and the processes and technologies available to help prevent and mitigate them.
-Avery Ebersol