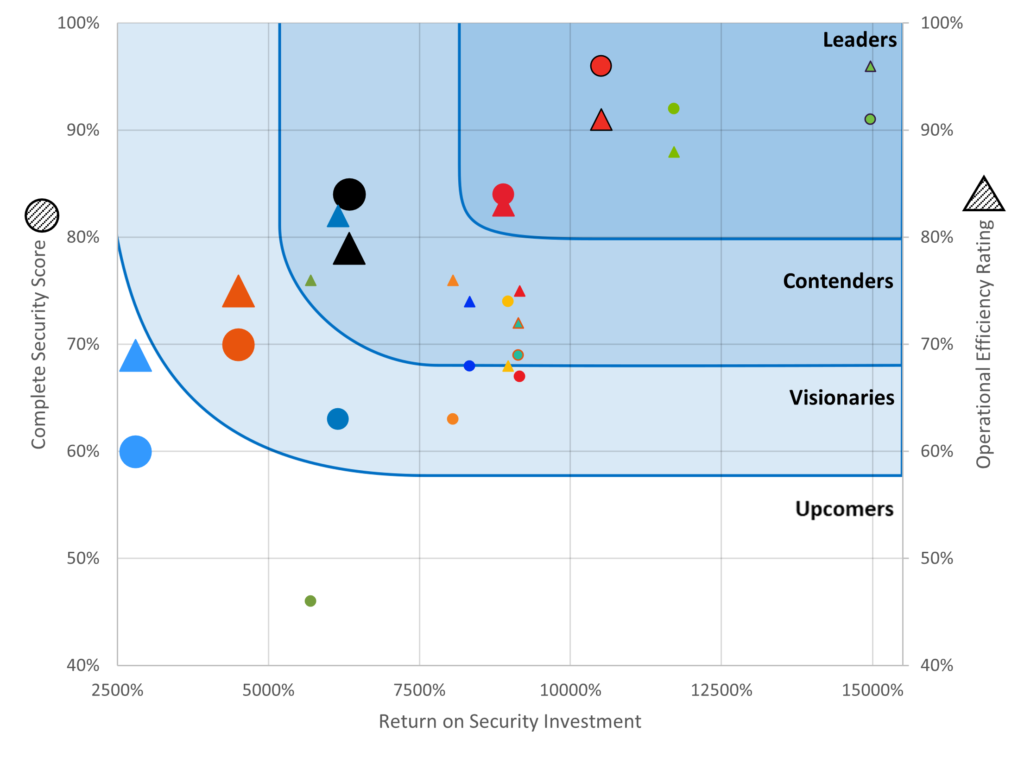
 Security Efficacy Leaders demonstrate a combination of superior security and ROSI. That is, these solutions provide stronger security technology at competitive pricing.
Security Efficacy Leaders demonstrate a combination of superior security and ROSI. That is, these solutions provide stronger security technology at competitive pricing.
Operational Efficiency Leaders demonstrate a combination of high-grade operational efficiency and superior ROSI. That is, these solutions combine ease of deployment, integration and resource management at competitive pricing.
Security Efficacy Contenders demonstrate excellent prevention and detection capabilities combined with an attractive ROSI.
Operational Efficiency Contenders demonstrate excellent operational efficiency for the ease of deployment, integration and strike a good balance between the technology and resource management with an attractive ROSI.
Security Efficacy Visionaries have either good security or ROSI. That is, solutions in this category were priced competitively or provided better than average security.
Operational Efficiency Visionaries demonstrate good operational efficiency standards around ease of deployment, integration or an excellent ROSI.
Security Efficacy Upcomers have lower security efficacy standards which contribute to lower ROSI.
Operational Efficiency Upcomers demonstrate lower operational efficiency standards for ease of deployment, integration and struck a poor balance between the technology and resource management, delivering a lower ROSI.