Security Vendor Services
Build Value with SecureIQLab
The cybersecurity market is flooded with options. SecureIQLab can help you stand out by demonstrating your solution’s return on security investment (ROSI), through our validation and publication of your technology’s operational and security capabilities. Our product evaluation services and publications, can help you:
Our range of one-time product maturity evaluations to cloud cyber range continuous validation offerings, may be used for product development roadmapping and strategic investment justification.
Our third-party validation of your solutions’ key differentiators, operational capabilities and security capabilities guide consumers to choose the correct security tools for their requirements and improve security outcomes.
Our market analysis and enterprise security understanding may be used for refining your go-to-market strategy.
In a recent engagement with a security vendor, we helped them to refactor their security offering and go-to-market successfully. With the right set of features and KPI’s directed at small-to-medium sized enterprises, their annual sales grew from ~$2.2 M to ~$6 M in the first year.
Publications Based on Methodologies that Matter
SecureIQLab works with governments, enterprise and security vendors to collaboratively develop methodologies that are relevant to the industry needs. These methodologies are based on industry standards such as OWASP, MITRE ATT&CK and Lockheed Kill Chain.
We invite Vendors to collaborate with SecureIQLab and to refine these validation methodologies whether or not the vendors’ products are being validated. There is no need to participate in our validation of security solutions in order to assist in the iteration process of our test methodologies.
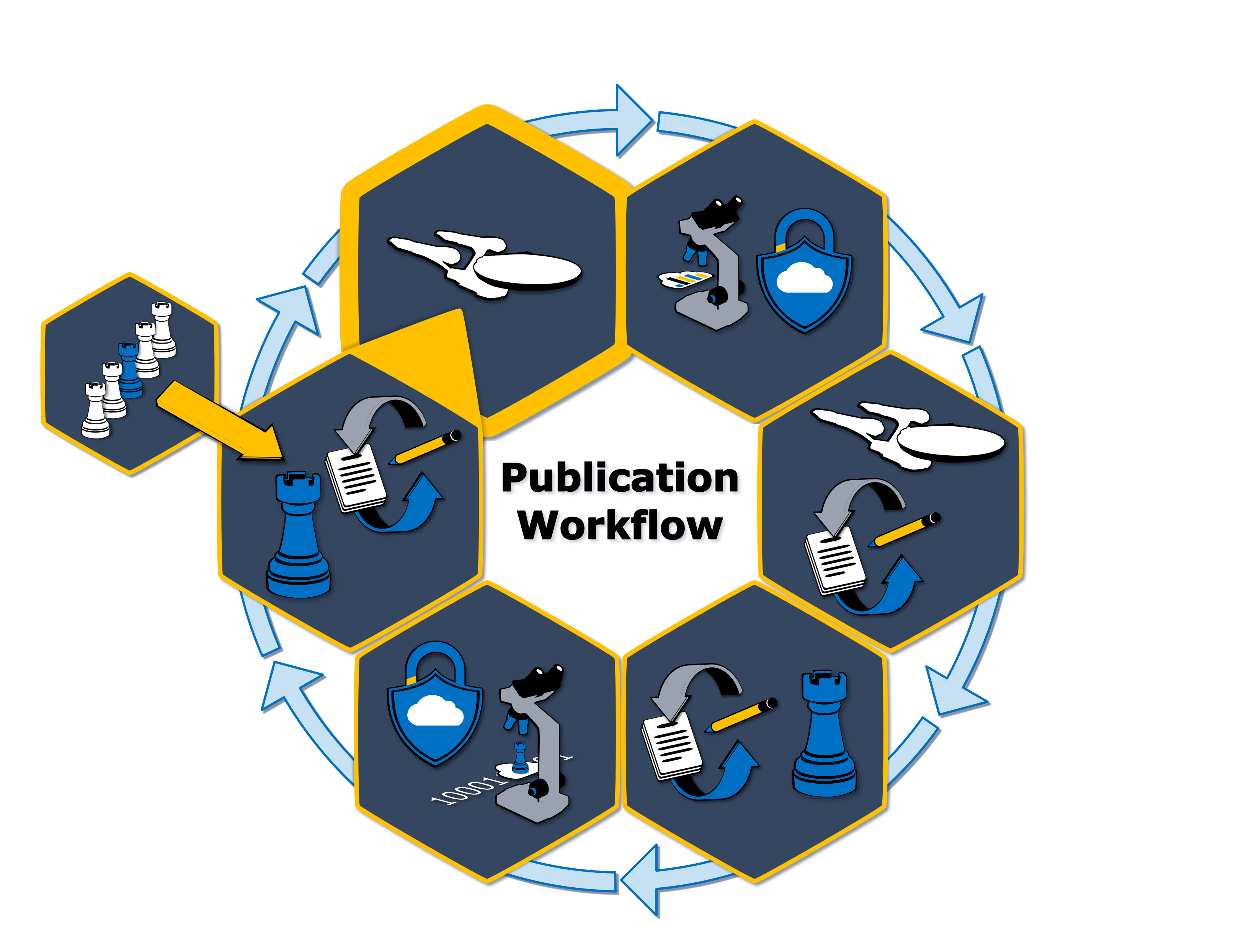
Below is the full methodology creation through validation and publication process:
Publication Workflow
1. Validate Enterprise Requirements
2. SecureIQLab Analysis
3. Enterprise Feedback
4. Iterate Methodology
5. Product Validation
6. Vendor Feedback
7. Determine Key Differentiators
8. Publication
Click on image for details
Publication

Marketing rights for individual and comparative reports available.
Validate Enterprise Requirements

Governments and enterprises drive workflow, technology, and cloud security requirements.
SecureIQLab Analysis

SecureIQLab completes a market, operational and technology analysis to create a draft methodology
Iterate Methodology

SecureIQLab works with vendors to iterate the methodology.
Product Validation
SecureIQLab validates vendors' solutions.
Vendor Feedback

SecureIQLab executes and completes the validation with an extensive feedback cycle with vendors. Key vendor differentiators will be featured in the individual resulting reports.
Determine Key Differentiators

Vendors determine with SecureIQLab key vendor differentiators to validate.
Enterprise Feedback

Enterprises provide SecureIQLab with feedback on the methodology.
Elevate Your Brand with SecureIQLab

- Brand development through custom individual or comparative testing
- Public test publications
- Highlight security efficacy
- Showcase operational efficiency
- Validate product features
- Demonstrate return on security investment (ROSI)
- Validate maturity and product capabilities against advanced attacks
- Simulate attacks against the products continuously based on emerging tools, tactics, procedures
SecureIQLab CyberRisk Validation Overview
- Application programming interface (API) Security
- Cloud Web Application Firewall
- Advanced Cloud Firewall
- Security Service Edge (SSE)
- Secure Access Service Edge (SASE)
- Kubernetes & Container Workload Protection
- Extended Detection and Response (XDR)

