In this post, we break down what the recently-discovered FireEye and supply chain attack shows about your cyberattack surface.
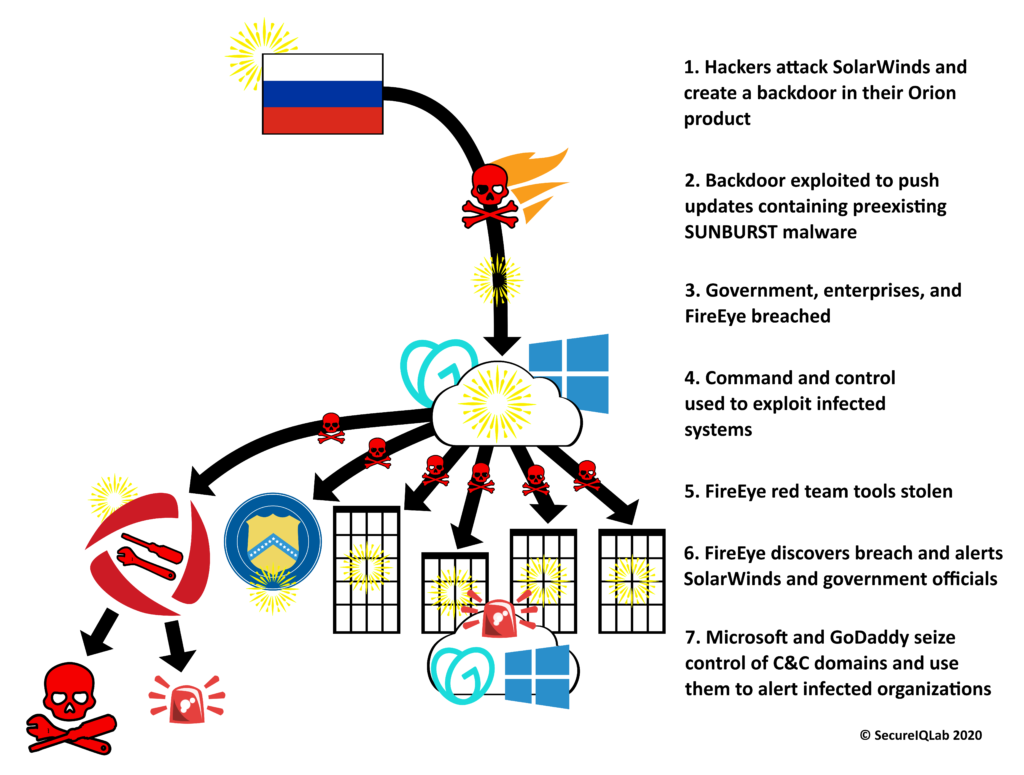
The above figure shows what we know so far about the stages of the FireEye attack.
To summarize the above diagram, Russian attackers compromised SolarWinds and used their trusted software, Orion IT, as the vehicle to compromise multiple organizations. News reports state that over 18,000 SolarWinds customers were affected. SolarWinds customers who were affected included at least 6 federal agencies and the United States Commerce, Treasury, and Energy departments. Private companies listed as potentially effected run the gamut from Proctor and Gamble to Best Western. Most importantly for our discussion today, they include the security vendor FireEye. Attackers used SolarWinds’ software update mechanism to push out a malicious update that allowed them inside the systems of SolarWinds’ customers like FireEye. Once inside, the attackers used privilege escalation to accomplish their goals.
FireEye provides security controls. FireEye also conducts their own red team research for the security of their products and other solutions. Red team research is attack research, where security companies develop new attacks as a step towards preparing to defend against them. The vulnerabilities discovered by FireEye’s red team, that hackers were able to weaponize, are part of what is called FireEye’s tool chain.
Much to FireEye’s credit, once they discovered the breach of their tool chain, they went public with the stolen red team tools. Analysis of these tools indicates that although a good portion of these tools are open source, and hence already available, there were tools that could cause future issues, including FireEye’s retooling of the open source tools. Our research also indicates that retooling of such open source tools is highly effective against the endpoints that typically act as the last layer of defense before a breach happens
What does possible security control compromise mean to the cybersecurity practitioner?
Complexity and sophistication of operations and tools create new attack surfaces. In this era, a breach in one organization may have massive ripple effects on other organizations downstream. Extrapolating from where we are currently, Year 2020 and forward is going to be the era of supply chain attacks, including through security controls.
Automation within supply chain management must be verified before it may be trusted. FireEye being hacked downstream of the SolarWinds hack is the kind of attack that will proliferate as we rely on automation without checks.
It’s not uncommon to see stolen red team tool chains get integrated with open source tools and then end up for sale on the dark web. The leak of the FireEye tool chain could result in the kind of similar collateral damage that was caused by CIA vault leak. Attackers will potentially unleash a spike of attacks towards SMBs and the general public as these tools become available to script kiddies.
Out of all the generic attack surfaces within the computing environment, the security control attack surface has become a worthwhile target for nation state actors. Zerodium’s bounty program for AntiVirus RCE/LPE vulnerabilities provides foreshadowing of future issues.
The cybersecurity industry has come a long way in collaborating against threats and in protecting users in the evolving landscape. However, what we lack today is a fundamental understanding that the threat ecosystem is proliferating more by the day, to the point where we need to start addressing the attacks that are targeting the noncore assets, such as the supply-chain, that have the inherent ability to bypass security controls.
At SecureIQLab, we advise our clients on not only understanding their current cyberattack surface, but also help protect against targeted attacks against their security controls using our proprietary validation framework and test methodologies while mapping these attacks to MITRE, OWASP, NIST, and other frameworks. This reduces risk and improves your overall cybersecurity posture, resulting in effective return on investment in security controls.



