Services for Governments and Enterprises

Security awareness training:
- Cyber hygiene best practices
- Phishing education and simulation
- Security awareness for the new remote workforce
Red Team training
- How to build a Red Team
- How to simulate attacks
- Red Team best practices
Process assessment and best practices:
- Architecture
- Security strategy
- Incident response
- Cloud security migration
- Application migration


Assessment services and Tools:
- SpartaIQ
- Workflow and Use case validation Proof of Concepts
- Cloud Security stack validation.
- Continuous cyber range validation™
- Cyber War games and Battleground/Cyber Attack Assessment
Endpoint CyberRisk Assessment :
- User hygiene/self-management
- Forensic readiness
- Defensive posture and Physical security
- Insider threat/Exfiltration
Threat Intelligence Feeds
- Malware Data – Windows & Mobile
- Phishing URLs
- Malicious & Suspicious URLs
- Botnet Controller Intelligence Feed
Cybersecurity Lab as a Service (CLaaS)
Improving Cloud Security through Validation Collaboration
We work with enterprises, governments, and security vendors to publish complementary security validation reports on vendor technologies
We work with public and private organizations help identify relevant areas of coverage, identify workflows and validate scenarios
Our team also invites these organizations to provide feedback on our testing methodologies
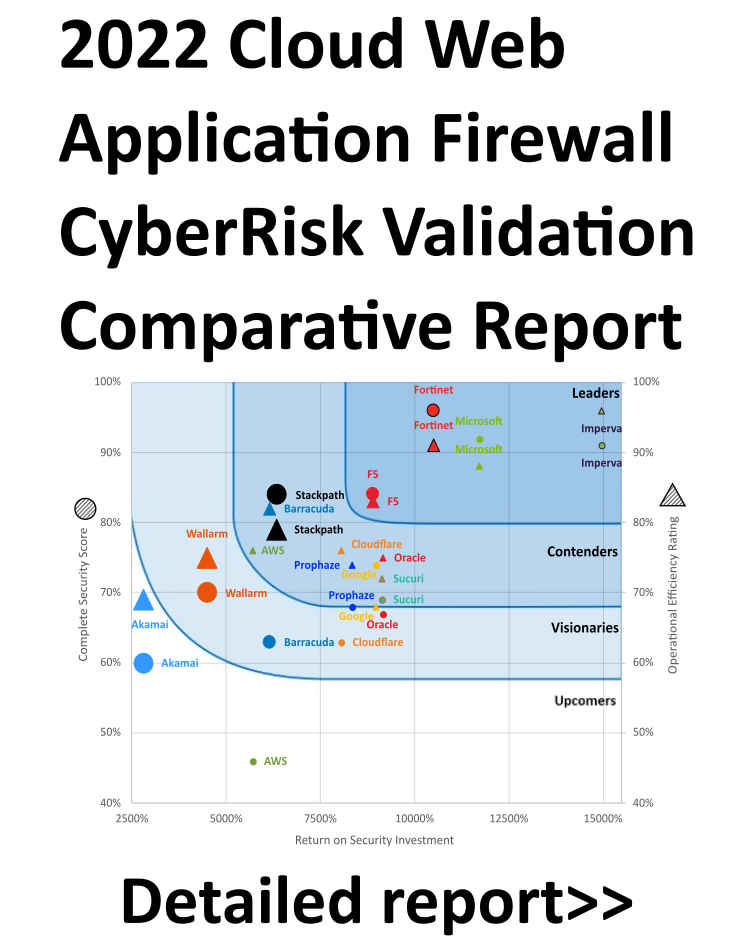
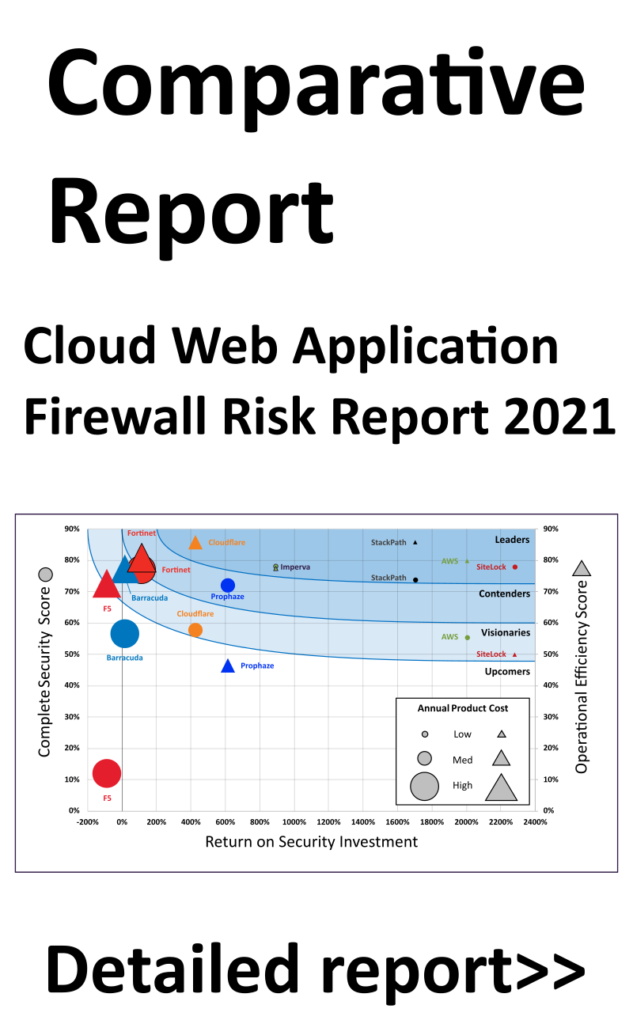
Published results are shared as complementary individual reports and a comparative CyberRisk Readiness Quadrant
Individual test verification reports provide detailed validation of security against nation state attacks, advanced attacks, results that map to NIST, MITRE ATT&CK frameworks and the Lockheed Martin Kill Chain, and highlight validated key vendor differentiators.
The Enterprise CyberRisk Ripple helps organizations understand ROSI (return on security investment) on operational and security levels.
There is nothing magic about our quadrant. We use science.
Enterprise CyberRisk Ripple
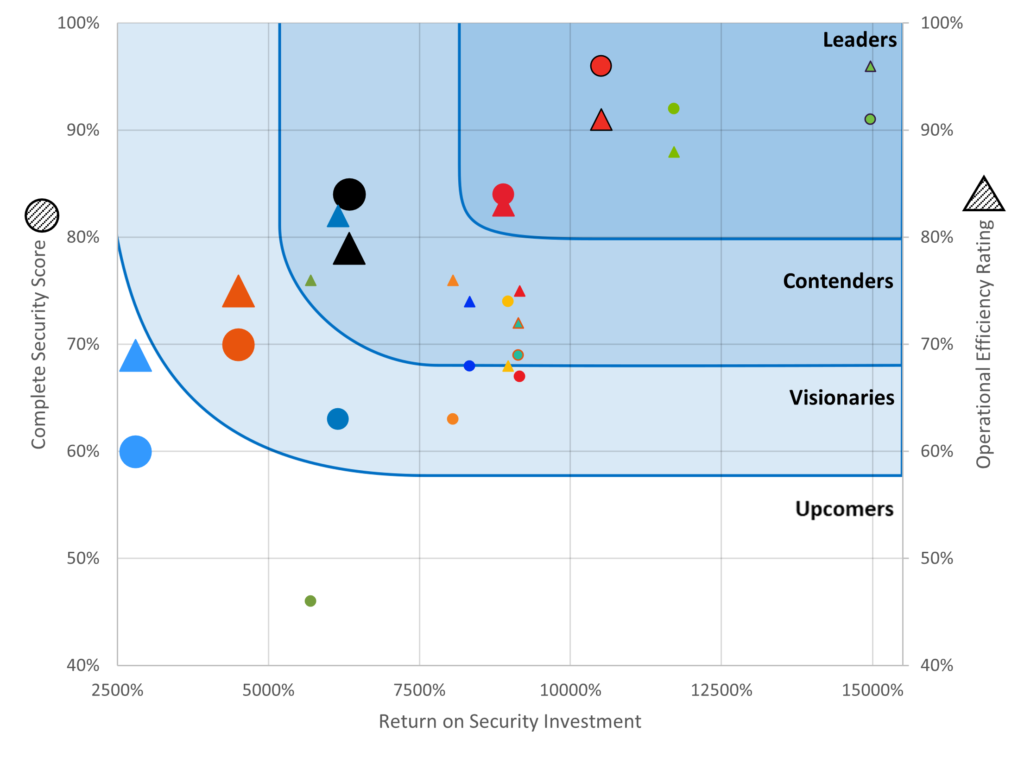 Security Efficacy Leaders demonstrate a combination of superior security and ROSI. That is, these solutions provide stronger security technology at competitive pricing.
Security Efficacy Leaders demonstrate a combination of superior security and ROSI. That is, these solutions provide stronger security technology at competitive pricing.
Operational Efficiency Leaders demonstrate a combination of high-grade operational efficiency and superior ROSI. That is, these solutions combine ease of deployment, integration and resource management at competitive pricing.
Security Efficacy Contenders demonstrate excellent prevention and detection capabilities combined with an attractive ROSI.
Operational Efficiency Contenders demonstrate excellent operational efficiency for the ease of deployment, integration and strike a good balance between the technology and resource management with an attractive ROSI.
Security Efficacy Visionaries have either good security or ROSI. That is, solutions in this category were priced competitively or provided better than average security.
Operational Efficiency Visionaries demonstrate good operational efficiency standards around ease of deployment, integration or an excellent ROSI.
Security Efficacy Upcomers have lower security efficacy standards which contribute to lower ROSI.
Operational Efficiency Upcomers demonstrate lower operational efficiency standards for ease of deployment, integration and struck a poor balance between the technology and resource management, delivering a lower ROSI.