If there’s one thing I hate more than bad password advice it’s okra. But this is about cybersecurity, not culinary mayhem.
Thanks to the added security multi-factor authentication (MFA) provides, passwords have been given a new lease on life. Since passwords are going nowhere soon, let’s take the agony out of password creation and use. To those of you who thought passwords would be dead by now… sorry your predictions are just plain wrong. Fear not though, intelligent sounding, but wrong, predictions can land you a high-paying job as an analyst! Just ask me Just ask any major analyst firm.
Seriously folks, passwords are going to be around for a long time and that means we can parrot bad password advice and turn users into basket cases, or we can think and act upon logic. Let’s take a quick stroll through the litany of bad password advice that should have died with Windows Vista.
We’ll start with “Must contain uppercase, lowercase, numbers, symbols.” This level of complexity advice actually had a place at one time but has been perpetuated by the math impaired. A bit of history. At one time the cost of storage devices was high, processing power was low, and we took TRS 80s seriously. For reasons of cost, passwords were limited to 8 characters because each password increased the amount of disk space required by an ever-expanding database. Databases consumed precious processing and memory. Additionally, 8 characters was long enough if your character set was sufficiently large. There are only 209 billion possible 8-character passwords if all you use is lowercase or uppercase letters. If you use both uppercase and lowercase letters, you’re up to almost 53.5 trillion possible unique passwords. If you use all four characters sets, you have a respectable 6.6 quadrillion possible unique passwords. Twelve of those passwords can actually be remembered.
Now consider a password that has only lowercase letters but is 12 characters long. There are now about 95 quadrillion unique passwords that can be created. Instead of ~#f5Th9_ you can use the much stronger alexandraismywife, and remember it too. Length is king, and passphrases, which are passwords, do not need to be complex to create a much stronger password than any possible 8-character password using the full printable ASCII character set. alexandraismywife is easy to remember and at 17 characters log provides more than 170 million times more permutations than a complex 8-character password. In practice most people will use spaces between words, so now we have “alexandra is my wife” which at 20 lower case letters and a space in the character set has between 6.3 trillion to 39 quintillion times more permutations than a complex 8-character password. I hear you asking “why did you use a range instead of a concrete number. It has to do with attack choices. Even though a space is part of the 33-character symbol set, an attacker can choose to only use the space character in his/her attack. Simply using the 10 most commonly used symbols is effective and efficient.
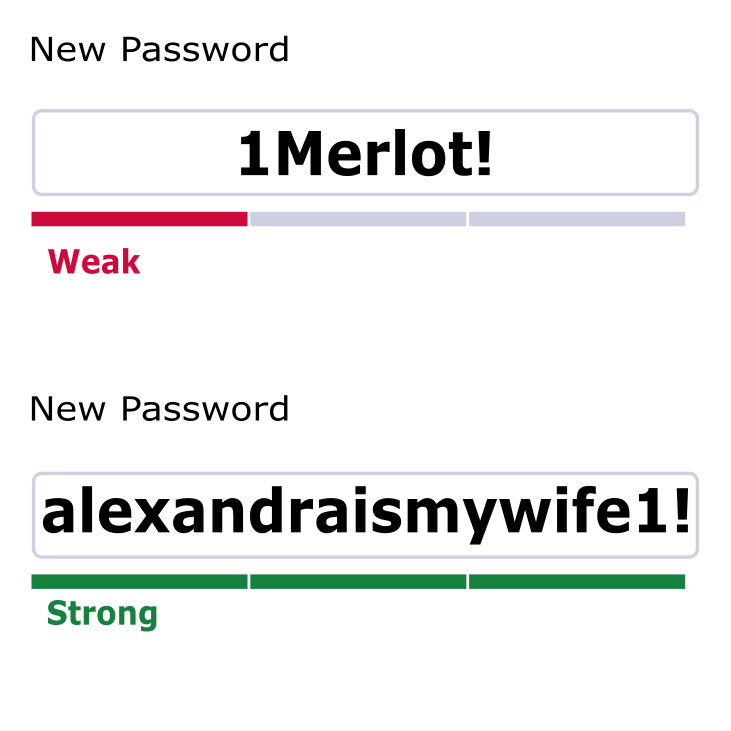 But frequently you can use a feeble password like “1Merlot!” but not a great password such as “alexandra is my wife1!”. Ignore the people that say adding 1! To the end doesn’t help. The purpose of 1! is to enable the use of a great password. It doesn’t weaken a 20-character password that precedes it. You might have to capitalize a letter, but that shouldn’t affect the ease of committing the password to memory. Note: for passwords less than 12 characters, make it complex.
But frequently you can use a feeble password like “1Merlot!” but not a great password such as “alexandra is my wife1!”. Ignore the people that say adding 1! To the end doesn’t help. The purpose of 1! is to enable the use of a great password. It doesn’t weaken a 20-character password that precedes it. You might have to capitalize a letter, but that shouldn’t affect the ease of committing the password to memory. Note: for passwords less than 12 characters, make it complex.
Yike!!! Did I just use my wife’s name in a passphrase? Do not use a name *for* a password is good advice, but “for” is not the same as “in.” You can use a name, birthday, anniversary, etc. *in* a password. Nobody is going to guess “jane pet ms fluffy again”. Use names, birthdays, etc. as part of a password if it helps you remember it. The key to creating a good passphrase is to make it a long original phrase. Making a silly, original password virtually eliminates password-induced trauma.
Now that you have a fantastic password write it down. Yeah, write it down 20 or thirty times and then destroy the paper. Writing information down helps commit information to memory. In fact, write it down many times for a few days in a row. You can write down passwords at home on paper and keep the paper, but there is a level of risk in doing so. The risk is if someone should have physical access to your computer and the written password. As long as you keep the written password away from your web cam there is no risk from remote hackers. I recommend keeping anything with a written password hidden when not in use.
To recap:
- Ditch complexity for length. Most experts suggest at least 20-characters, but honestly, make your password at least 16 characters long and I’ll give you a silver star. Do note, including all four characters sets isn’t bad, as long as it doesn’t interfere with making your passwords easy to type and remember
- Use your spouse’s name, kid’s name, or best of all, your anniversary if you’re married, *in* a passphrase if it helps you remember it.
- Write down your password… many times… for a few days in a row. Destroy the paper after each session.
One last comment. There’s a fairly obscure attack against passphrases called a passphrase token attack. Basically, the attack works by guessing whole words at a time instead of single letters at a time. I’ll write more about the passphrase token attack in a future blog, but if you are not familiar with that attack and someone brings it up, say “Show me the math.” Frequently people discussing passphrase token attacks make a mistake in thinking that four words are no better than a four-character password. Here’s the problem with their math. There are 95 printable ASCII characters. A four-letter password has 95^4 permutations. The English language has well more than a million words. Let’s go with a million. That’s 1,000,000^4, which of course is a bit more than 95^4. For reasons of math, it’s more secure to use at least 5-words. Don’t forget to watch the character count too. No matter what number of words you use, it should be at least 16 characters long.
Randy Abrams
Senior Security Analyst
SecureIQLab
Footnote: Alexandra is not my wife’s name, and Ms Fluffy is a great name for a Shar-Pei



