Company
Mission Statement
Company Vision
Company Values
WHO WE ARE
SecureIQLab is a US-based independent, third-party cloud security solution validation and advisory provider.
SecureIQLab cloud security methodology is tailored to what enterprises want, blending research, risk management, and data modeling performed by our deep bench of security experts.
SecureIQLab is a member of the Anti-Malware Testing Standards Organization (AMTSO) and the Cloud Security Alliance (CSA).
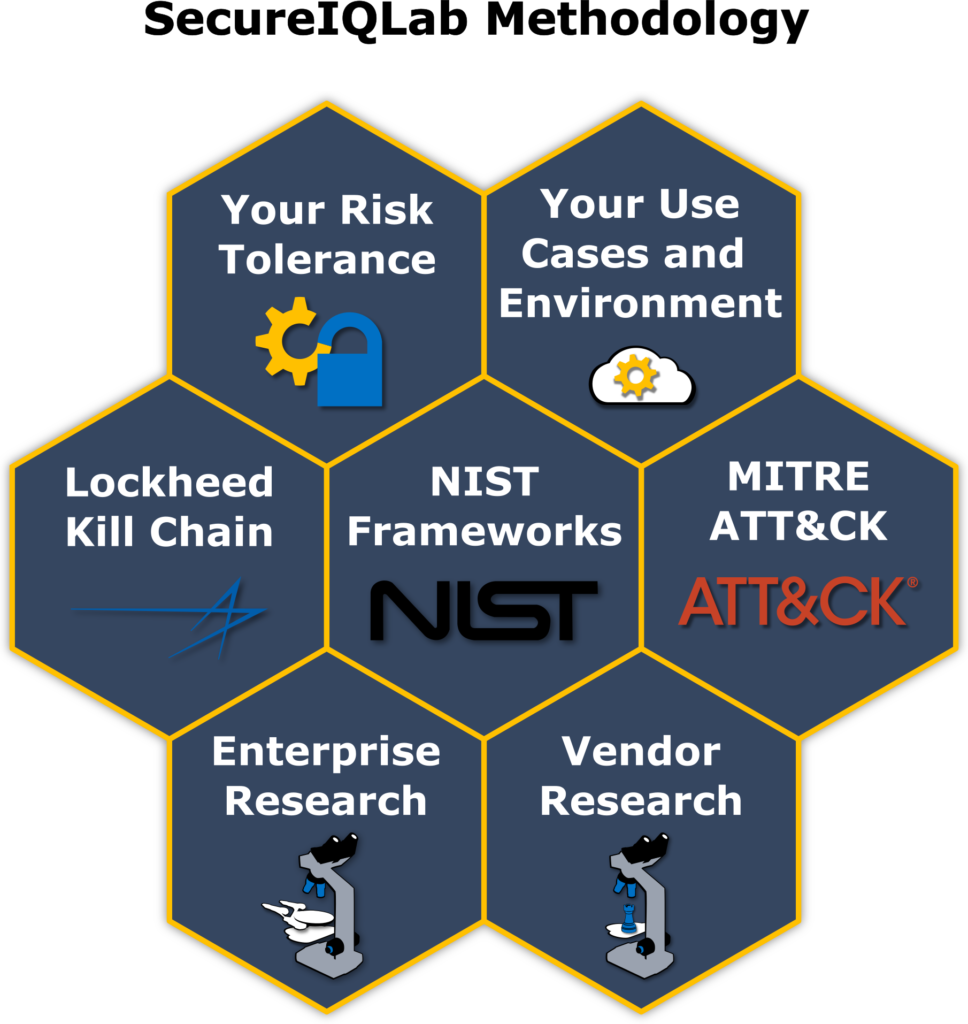
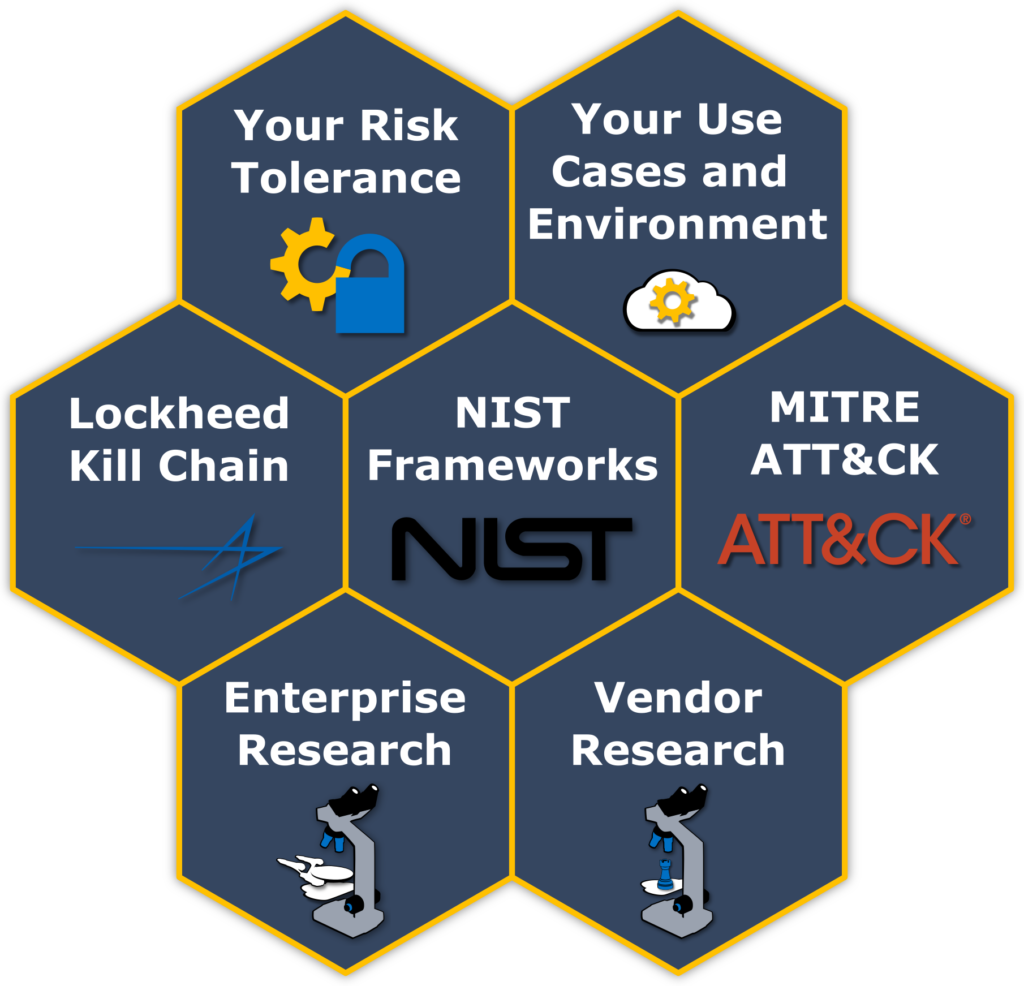
OUR METHODOLOGY
In today’s hyperconnected world, we enable clients identify and close gaps through a holistic approach to cloud security.
Our validation methodologies result from our work with enterprises and security vendors. This collaboration builds on respected frameworks such as NIST, MITRE ATT&CK and the Lockheed Kill Chain to meet your specific business requirements and needs.
We offer guidance on making right investments in your cloud security framework, hence reducing risk exposure. Doing this requires use-case-driven, intelligence-led, proven risk mitigation methodology.
We derive and focus on cloud security solution metrics that matter to enterprises. We don’t just use a one-size-fits-all approach based on test cases against a unified methodology.
We take the cloud security you use, focus on how it is intended to protect you, how it fits together with your other protections, and what risks you are willing to accept versus what risks you actually have.
We validate these cloud security solutions under your real-world use. This use-case-driven, intelligence-led, proven risk mitigation methodology yields measurable data enabling us to quantify our results.
OUR COMMITMENT
Our philosophy is simple, we focus on one thing – creating long term value through an undying commitment to our clients’ success.
Our customer-centric approach puts the needs of our clients first and encourages strong communicative relationships.
TECHNOLOGY EXPERTISE: PROVEN YET CONSTANTLY EVOLVING
Delivering on-demand, real-time enterprise focused cybersecurity expertise for 50+ years.
Evaluating Information Technology (IT) vs System Operations (SysOps) vs Development Operations (DevOps) needs
Methodology, validation use-case and technology-based test case creation
End-to-end technology stack know how
Enterprise focused cybersecurity briefs that are usable from IT personnel to Operations and all the way to CISOs/CIOs
CLIENTS
COUNTRIES
SUCCESSES
PEOPLE
50+ years of combined cybersecurity experience
15+ years of combined 3rd party market/technology/solution validation experience
10+ years of combined product and technology strategy from “Conception” to “Launch” Stages
MARKET KNOW-HOW
Cyber security landscape, market overview and direction
Total Addressable Market (TAM) value, growth rate along with 1, 3 and 5 year projections
Solution growth cycle
Enterprise adoption
Small-to-Medium to Fortune-500 enterprise exposure
Enterprise value metrics derived from all major verticals
Enterprise use cases vs security vendor product features/capabilities