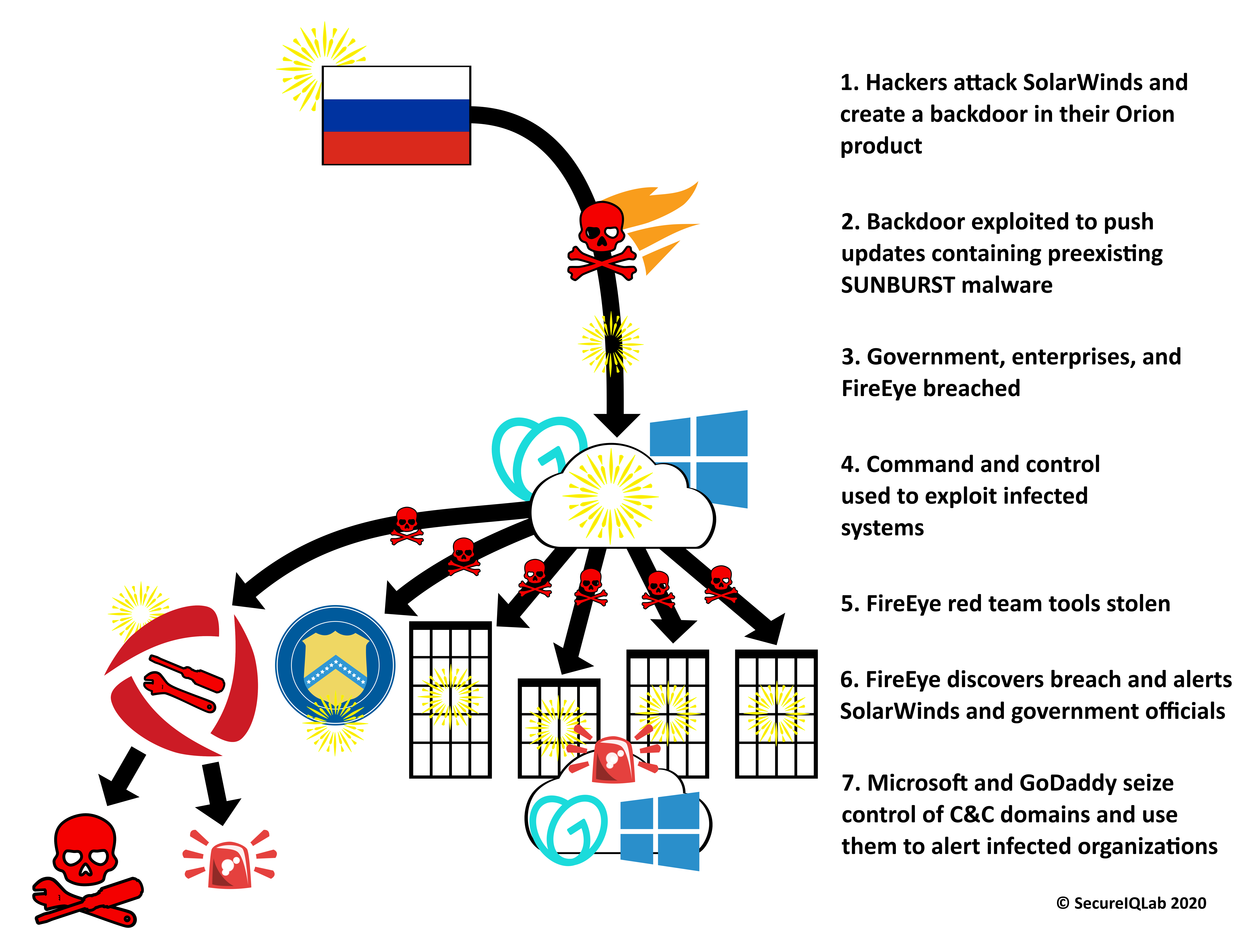
Cybersecurity Controls are the next Frontier of the Evolving Cyberattack Surface (Part 2)
In this post, we break down what the recently-discovered FireEye and supply chain attack shows about your cyberattack surface. The above figure shows what we know so far about the…