“Change is the only constant.”
“Change is the only constant.”
— Heraclitus
Your cyberattack surface is the part of the computing environment that can be leveraged by an attacker to take advantage of any vulnerabilities. It is the part of your computing network that is exposed. This can include any code, software, or hardware that is added to the environment. Any software that has been granted privileges within your computing environment increases your cyberattack surface.
From a computing point of view, privilege provides the ability to run whatever you want within the computing environment. Privilege escalation is the acquisition of higher-level privileges that are otherwise not applicable for an entity within that environment. Entity here may mean user, persona, or tokens.
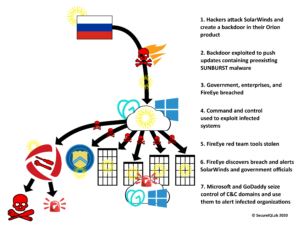
Attackers, in their penetration attempts, will generally attempt to use your cyberattack surface to engage in privilege escalation. Security controls are the mechanism that provide safeguards and countermeasures within a computing environment. Security tools are the means to enforce security controls. Depending on their deployment and management, security controls can present their own attack surface. Recent hacking events, like the FireEye hack, have underscored the importance of understanding your cyberattack surface within your computing environment. In an upcoming blog post, we will be breaking down this cyberattack surface in the context of the FireEye and supply chain attack that had a devastating worldwide effect on organizations. We will also give a security practitioner’s viewpoint on how to mitigate the risks of a third-party vendor supply chain ecosystem within your computing environment.
At SecureIQLab, we advise our clients on not only understanding their current cyberattack surface, but also help protect against targeted attacks against their security controls using our proprietary validation framework and test methodologies while mapping these attacks to MITRE, OWASP, NIST, and other frameworks. This reduces risk and improves your overall cybersecurity posture, resulting in effective return on investment in security controls.